Here’s how to bypass SSL errors on your browser
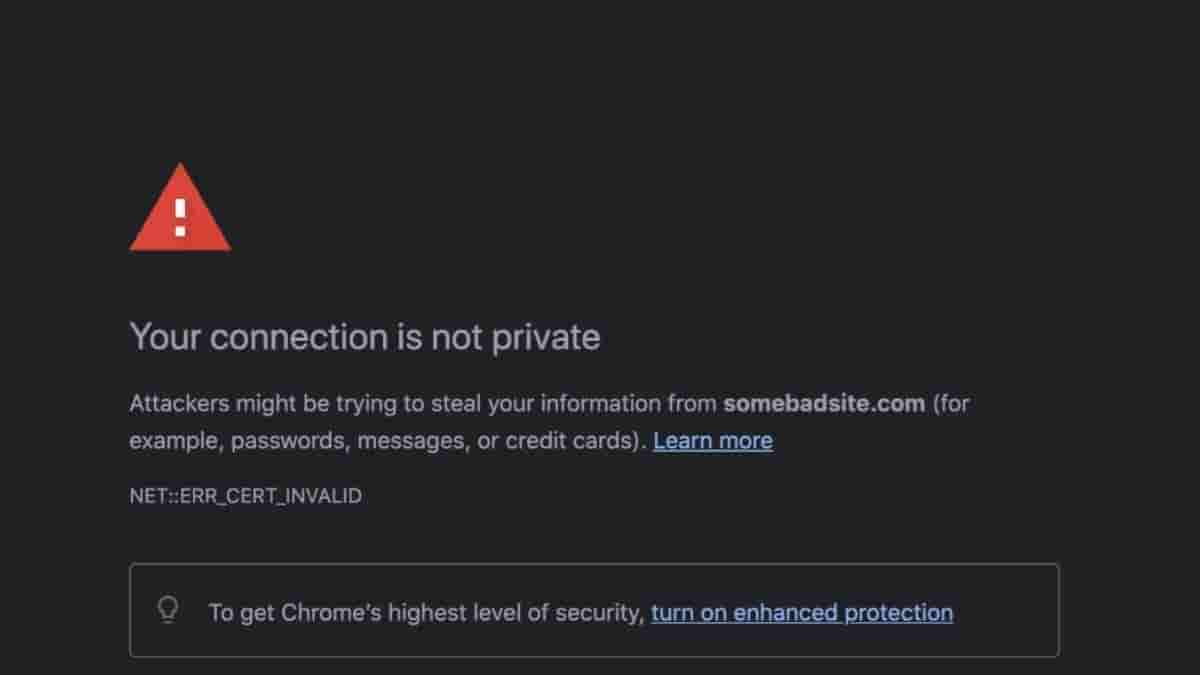
Browsers often warn us when we visit an insecure site. Irrespective of the site starting with the secure url https:// , the security of the website still depends on the certificate issued to the site. It does not depend on the sites configuration in port 80 or port 443.
The reason for a certificate going invalid amounts to hundreds. Some such scenarios are:
- Certificates expiring: Usually SSL certificates comes with an expiry date even when you have purchased them. Paid-systems carry on certificate issue with auto-renewal options while free services comes in with the option of manually renewing them. Until we make sure that our certificates are valid in regards to expiry date, the site’s visitors will receive a warning that your site is insecure.
- Links which are insecure: In a scenario, where your certificate is valid, links like images in your sites might exist without the https:// scheme, thus making your site insecure.
- Unfamiliar Certificate Authority: This refers to organizations, which have already established their own network. Browsers are aware of this fact even before you install them. When you configure your own CA, for example for a local network in an organisation, browsers will not rely on you and will give SSL errors even if the certificate is configured properly.
Here’s a trick to bypass such warnings:
These are just warnings that a browser presents to a user. Some browsers lets the user pass right after clicking on the “Accept and Continue” button. In certain cases, browsers like Chrome doesn’t even present the Continue button. For such scenarios, there exists a bypass. You can opt to type “thisisunsafe” anywhere on the window and the browser will let you pass to visit the page.
Through this bypass, an exception for the particular domain is added to chrome’s internal memory. You can choose to remove this exception by clicking on the padlock icon and Re-enabling Warnings links. The situation is same for Firefox albeit with a little alteration in the UI etc.
This chrome dev team has deliberately created this bypass for testing purposes. Previously this bypass existed with the keyword “badidea”. However they updated it as it has been taken as a method of abuse.
Experts also suggests that setting up certificates properly instead of using the bypass everytime is more convenient. They have also mentioned a bug that makes caching function improperly wit SSL errors. Although caching issues aren’t much to be worried about, SSL errors still needs to be taken very seriously.
The existence of the bypass is not meant to falicitate abuse of the bypass. Using this feature on your own website for testing purposes is fine. But, you should not use it to go through such warnings on every other site.
The warning screens that puts barriers on the choice of visiting certain websites are known as interstitials.
A small procedure exists for those who wants to remediate the certificate issue for self signed certificates on local systems. A user can import the certificate into your CA keychain. This will make the certificate valid across many browsers.
After this is executed, the browser will accept the connection as a secure connection. Following it a user won’t receive further insecure connection warnings. Thus you will be free from SSL warning interstitials. However, it may be required to carry out this step for every domain.


